[align=center]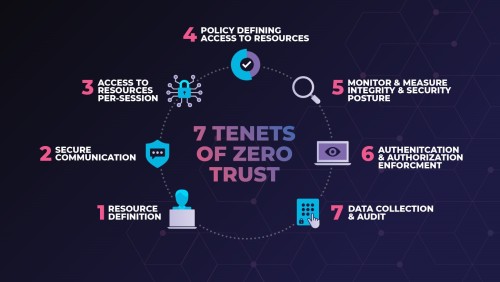
Zero Trust Architecture Security Core Concepts
Published 9/2024
Duration: 56m | Video: .MP4, 1920x1080 30 fps | Audio: AAC, 44.1 kHz, 2ch | Size: 1.02 GB
Genre: eLearning | Language: English[/center]
Master the Core Concepts of Zero Trust to Strengthen Your Cybersecurity Framework Against Modern Threats.
What you'll learn
Identify Weaknesses in Perimeter-Based Security: Understand why traditional security models fail to protect against modern threats in today's digital landscape.
Understand Core Zero Trust Principles: Explore the key concepts of Zero Trust, like continuous verification, least privilege access, and network segmentation.
Design and Implement a Zero Trust Architecture: Gain the skills to build and deploy a Zero Trust framework, enhancing security and reducing the attack surface.
Apply Zero Trust in Real-World Scenarios: Implement Zero Trust to protect against internal and external threats while securing critical data.
Requirements
A basic understanding of cybersecurity concepts and terminology.
Familiarity with network security principles is helpful but not required.
Access to a computer with an internet connection for hands-on practice.
No prior experience with Zero Trust Architecture is needed; this course is suitable for beginners and professionals looking to enhance their skills.
Description
Zero Trust Architecture Security Core Concepts
is designed to revolutionize your approach to cybersecurity by moving beyond outdated, perimeter-focused defenses. In the face of today's evolving digital threats, traditional security models are no longer sufficient. This course offers you a comprehensive introduction to Zero Trust Architecture, an approach that challenges the conventional assumption of trust, ensuring that every access request is thoroughly verified, whether inside or outside your network.
Through a series of expertly crafted lessons, you'll gain essential knowledge and hands-on skills that will allow you to confidently implement Zero Trust principles in your organization.
In this course, you'll
Examine the Limitations of Perimeter-Based Security
Discover why legacy security models based on clear network boundaries no longer effectively safeguard against modern cyber threats. You'll learn how these boundaries fail to protect sensitive data and resources from sophisticated attackers who exploit the gaps in traditional defenses.
Explore Core Zero Trust Principles
Gain a deep understanding of the foundational pillars of Zero Trust, including continuous verification, least privilege access, and comprehensive security monitoring. You'll also learn about the various resources and tools that can support your implementation of these principles.
Implement Zero Trust Practices
Using real-world examples and practical steps, this course will guide you through the process of designing and implementing a Zero Trust architecture. You'll explore how to build a robust, segmented network that mitigates the risk of breaches and reduces the attack surface, protecting your organization from both internal and external threats.
By the end of this course, you'll be equipped with the knowledge and practical skills necessary to design and implement Zero Trust Architecture, fortifying your organization's security posture against the most advanced and persistent cyber threats in today's landscape. Take the step toward a more secure future by embracing the Zero Trust model today.
Who this course is for
Cybersecurity professionals looking to expand their knowledge of modern security frameworks.
IT administrators who want to implement Zero Trust strategies in their organizations.
Beginners in cybersecurity who are eager to learn foundational concepts of Zero Trust Architecture.
Security consultants and architects aiming to stay current with cutting-edge security models and improve client solutions.
Business leaders and decision-makers who want to better understand Zero Trust principles to enhance their organization's security posture.
Homepage
Screenshots
Buy Premium From My Links To Get Resumable Support and Max Speed
https://rapidgator.net/file/3c07f44940b … 1.rar.html
https://rapidgator.net/file/0be4a8ff123 … 2.rar.htmlhttps://nitroflare.com/view/E3F36D6347C … .part1.rar
https://nitroflare.com/view/7D12637573E … .part2.rar

