
6.88 GB | 00:35:21 | mp4 | 1920X1080 | 16:9
Genre:eLearning |Language:English
Files Included :
1 - Communication plan (75.42 MB)
10 - Injection XPath Injection Log Injection Input Validation (103.77 MB)
11 - Insecure Design Overivew CWEs Shift Left Security Threat Modeling Manifesto (136.6 MB)
12 - Insecure Design Secure Design Process Security Controls Metrics Examples (149.96 MB)
13 - Security Misconfiguration Overview CWEs Types Reallife attacks (127.66 MB)
14 - Security Misconfiguration Hardening Zero Trust Defense in Depth Practice (258.83 MB)
15 - Vulnerable Outdated Components (240.67 MB)
16 - Identification Authentication Failures (257.88 MB)
17 - Software Data Integrity Failures (137.08 MB)
18 - Security Logging Monitoring Failures (167.51 MB)
19 - ServerSide Request Forgery SSRF (163.03 MB)
3 - OWASP Top 10 Overview (145.75 MB)
4 - Broken Access Control (459.26 MB)
5 - Cryptography Failures Theory Sensitive Data Data Breach Types of Failures (115.89 MB)
6 - Cryptography Failures Practical Examples SQL Injections TLSSSL HTTPS (153 MB)
7 - Cryptography Failures Examples Password Encryption Hashing Salting (208 MB)
8 - Injection Overview Fuzzing CWEs Impact Injection Types Command Injection (147.87 MB)
9 - Injection Cross Site Scripting Types of XSS SQL JPA NoSQL Injections (145.8 MB)
21 - API12023 Broken Object Level Authorization Part 1 (202.77 MB)
22 - API12023 Broken Object Level Authorization Part 2 Practice (93.73 MB)
23 - API12023 Broken Object Level Authorization Part 3 ZeroTrust UUIDs (260.57 MB)
24 - API22023 Broken Authentication Part 1 Basics Impact Types of Attacks (202.63 MB)
25 - API22023 Broken Authentication Part 2 Case Studies OAuth OpenID (252.09 MB)
26 - API22023 Broken Authentication P3 Practice JWT Tokens Timing Attacks (355.21 MB)
27 - API32023 Broken Object Property Level Authorization Part 1 (208.41 MB)
28 - API32023 Broken Object Property Level Authorization Part 2 Practice (221.01 MB)
29 - API42023 Unrestricted Resource Consumption Part 1 (297.77 MB)
30 - API42023 Unrestricted Resource Consumption Part 2 Practice (121.91 MB)
31 - API52023 Broken Function Level Authorization Part 1 (91.1 MB)
32 - API52023 Broken Function Level Authorization Part 2 Practice (101.63 MB)
33 - API62023 Unrestricted Access to Sensitive Business Flows Part 1 (99.42 MB)
34 - API62023 Unrestricted Access to Sensitive Business Flows Part 2 (266.6 MB)
35 - API62023 Unrestricted Access to Sensitive Business Flows Part 3 Practice (118.42 MB)
38 - API92023 Improper Inventory Management Part 1 (300.19 MB)
39 - API92023 Improper Inventory Management Part 2 Practice (128.38 MB)
40 - API102023 Unsafe Consumption of APIs Part 1 (330.43 MB)
41 - API102023 Unsafe Consumption of APIs Part 2 Practice (147.87 MB)
42 - Bonus lesson (47.62 MB)
[align=center]
Screenshot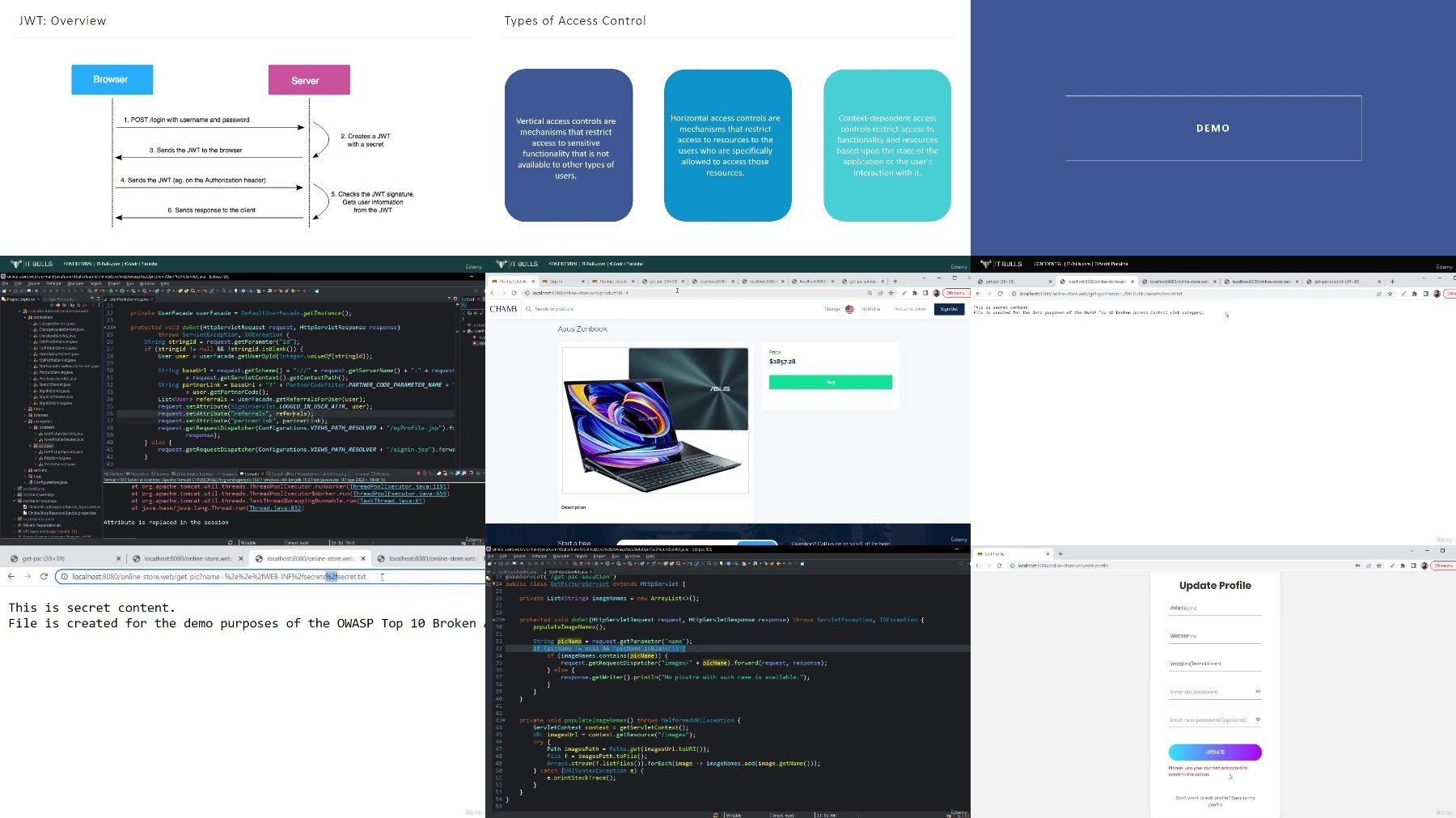
[/align]
https://ddownload.com/l4pmvoq8cmuu/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part1.rar https://ddownload.com/b9n76qlrie28/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part2.rar https://ddownload.com/1e2gd0fkfrzk/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part3.rar https://ddownload.com/6zgql3pbqd37/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part4.rar
https://rapidgator.net/file/d98e9df42503b8c795eb6630de4345d7/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part1.rar https://rapidgator.net/file/fe4d484fecc8c8f826fcf99aeb723436/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part2.rar https://rapidgator.net/file/d46c411e8b73fa26c815813908837081/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part3.rar https://rapidgator.net/file/5b8aec02459f2ddf3025b5b8a7202bb5/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part4.rar
https://turbobit.net/s0cnp7kzmw2b/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part1.rar.html https://turbobit.net/v9pp6o9zjmb2/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part2.rar.html https://turbobit.net/2ntojj7bpedh/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part3.rar.html https://turbobit.net/2q8y4us3nqpa/Udemy_Cybersecurity_for_Developers_From_Basics_to_Best_Practices.part4.rar.html

