
15.55 GB | 00:23:56 | mp4 | 1920X1080 | 16:9
Genre:eLearning |Language:English
Files Included :
1 - Welcome (53.91 MB)
2 - Course Navigation (72.26 MB)
3 - Course Overview (254.77 MB)
71 - Course Wrap Up (100.15 MB)
10 - Cybersecurity Cube (225.06 MB)
5 - Module Intro (61.88 MB)
6 - What is Cybersecurity (239.88 MB)
7 - The CIA Triad (218.51 MB)
8 - Cyber Incident Impact (160.26 MB)
9 - Key Cybersecurity Concepts (208.19 MB)
11 - Module intro (62.69 MB)
12 - Threat Agents (398.47 MB)
13 - Common Attack Vectors (291.78 MB)
14 - Common Vulnerabilities (185.28 MB)
15 - Common Equipment Vulnerabilities (301.75 MB)
16 - Common Software Vulnerabilities (292.93 MB)
17 - Race Conditions (260.85 MB)
18 - Social Engineering Techniques (332.15 MB)
19 - How Passwords are Hacked (340.07 MB)
20 - Malware (406.68 MB)
21 - Common Network Attacks (374.85 MB)
22 - Module Intro (84.64 MB)
23 - Protecting a Cybersecurity Domain (227.84 MB)
24 - What is a Cybersecurity Program (233.98 MB)
25 - Policies Standards Procedures Guidelines and Controls (90.52 MB)
26 - Types of Controls (154.3 MB)
27 - What is a Security Frameworks (236.14 MB)
28 - Risk Management (210.26 MB)
29 - Cybersecurity Lifecycles (90.45 MB)
30 - Basic Security Principles (196.47 MB)
31 - Module Intro (51.44 MB)
32 - IAM (148.63 MB)
33 - Authentication Authorization Accounting AAA (105.45 MB)
34 - Password Habits (704.17 MB)
35 - MultiFactor Authentication (121.38 MB)
36 - Password Enforcement (180.11 MB)
37 - Federation (155.95 MB)
38 - Access Control (361.95 MB)
39 - Access Control Models (274.07 MB)
40 - Physical Access Control (198.17 MB)
41 - Module Intro (94.12 MB)
42 - Confidentiality (312.81 MB)
43 - Data Lifecycle (279.68 MB)
44 - Encrypting Data (118.16 MB)
45 - Data Management (251.7 MB)
46 - Steganography (144.06 MB)
47 - Data Obfuscation (230.9 MB)
48 - Module Intro (52.77 MB)
49 - Integrity (168.85 MB)
50 - PKI and Digital Certificates (282.61 MB)
51 - Digital Signatures (143.59 MB)
52 - Database Integrity (404.26 MB)
53 - Module Intro (92.74 MB)
54 - High Availability HA (330.01 MB)
55 - Measuring Availability Five 9s and SLAs (207.18 MB)
56 - Redundancy (466.25 MB)
57 - Replication (194.1 MB)
58 - Incident Response (205.88 MB)
59 - Disaster Recovery (333.76 MB)
60 - RPO and RTO (148.62 MB)
61 - Backups (465.22 MB)
62 - Backup Types (272.08 MB)
63 - Database Backups (118.68 MB)
64 - Module Intro (92.48 MB)
65 - Physical Security (325.35 MB)
66 - Network Security (481.28 MB)
67 - Firewalls (224.76 MB)
68 - Remote access (398.82 MB)
69 - Equipment Hardening (37.08 MB)
70 - HostBased Security (379.59 MB)
[align=center]
Screenshot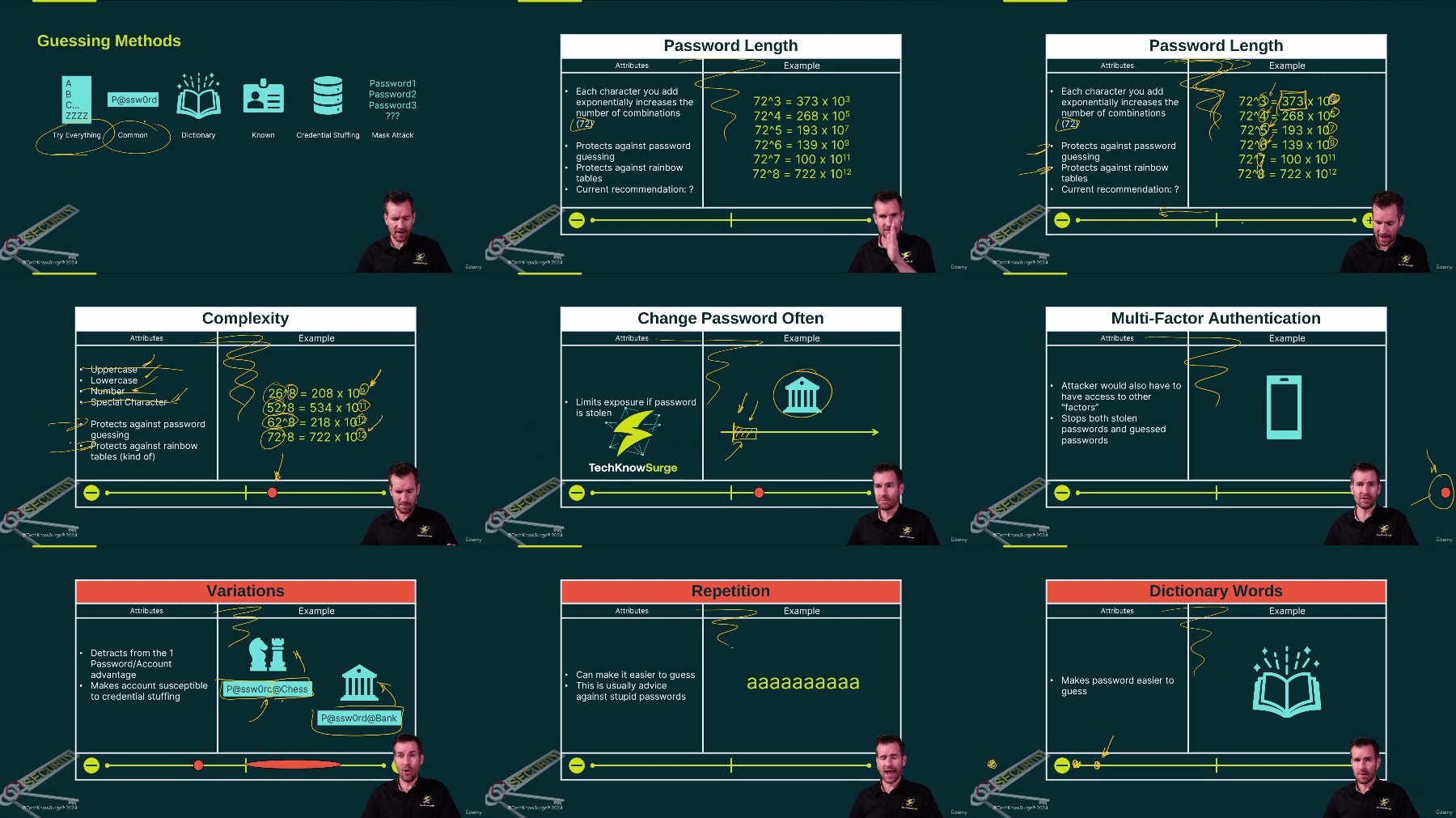
[/align]
https://ddownload.com/za5v5io6ixjj/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part01.rar https://ddownload.com/unz1pmkzrs2m/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part02.rar https://ddownload.com/yppukb4x97ih/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part03.rar https://ddownload.com/lm2brk4c4uoy/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part04.rar https://ddownload.com/h3dwfnlwcb6d/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part05.rar https://ddownload.com/3b25zqo9ekht/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part06.rar https://ddownload.com/w4s5aj9puv1d/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part07.rar https://ddownload.com/599vziu54pky/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part08.rar https://ddownload.com/l5tch5d3hbal/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part09.rar
https://rapidgator.net/file/77657bfa95d191a37684eb7648ceef62/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part01.rar https://rapidgator.net/file/05df691bba773bffff8b2b260636a256/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part02.rar https://rapidgator.net/file/1f7964f29dca798e8366ce74b39318e7/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part03.rar https://rapidgator.net/file/d2b257c153eb650bd170c1282420b606/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part04.rar https://rapidgator.net/file/7b85b7efb9a17c7a9f1a2c56807dd8a7/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part05.rar https://rapidgator.net/file/b4322b4272b1836f754360279f2777ba/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part06.rar https://rapidgator.net/file/fed7a8613a8eb88fc74199681fb0a746/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part07.rar https://rapidgator.net/file/44be40cd497b9a37fab7f285bb8a3713/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part08.rar https://rapidgator.net/file/82b0d9b2170ea8b8f12f80888730dd31/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part09.rar
https://turbobit.net/chwfq2vozi3f/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part01.rar.html https://turbobit.net/monuz67st24g/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part02.rar.html https://turbobit.net/bosd6a6v4806/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part03.rar.html https://turbobit.net/k0irazou38ii/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part04.rar.html https://turbobit.net/f030i5ibqxwy/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part05.rar.html https://turbobit.net/q2697bq3poga/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part06.rar.html https://turbobit.net/iq2jpkr4b8zq/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part07.rar.html https://turbobit.net/hle5gnjiax6q/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part08.rar.html https://turbobit.net/rt86ljc38jjq/.Foundations.of.Cybersecurity.by.TechKnowSurge.Andrew.Grimes.part09.rar.html

