
Open Source Intelligence, Ethical Hacking and Cyber Law
MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz
Language: English | Size: 10.8 GB | Duration: 20h 35m
Learn OSINT - Open Source Intelligence, Ethical Hacking, Cyber security and Cyber Law with Live Hacking on 200+ websites
What you'll learn
Cyber Law & IT Act Overview
Cyber Law Objectives
Intellectual Property Right
Cyber Security Strategies
Policies To Mitigate Cyber Risk
Network Security
Information Technology Act, 2000
Digital & Electronic Signatures
Offences & Penalties
Cyber Crimes FAQs
OSINT (Open-Source Intelligence) tools and techniques
Software tools and browser add-ons for Open Source investigations
Investigation techniques for Social Media sites including Facebook, LinkedIn, TikTok and Twitter
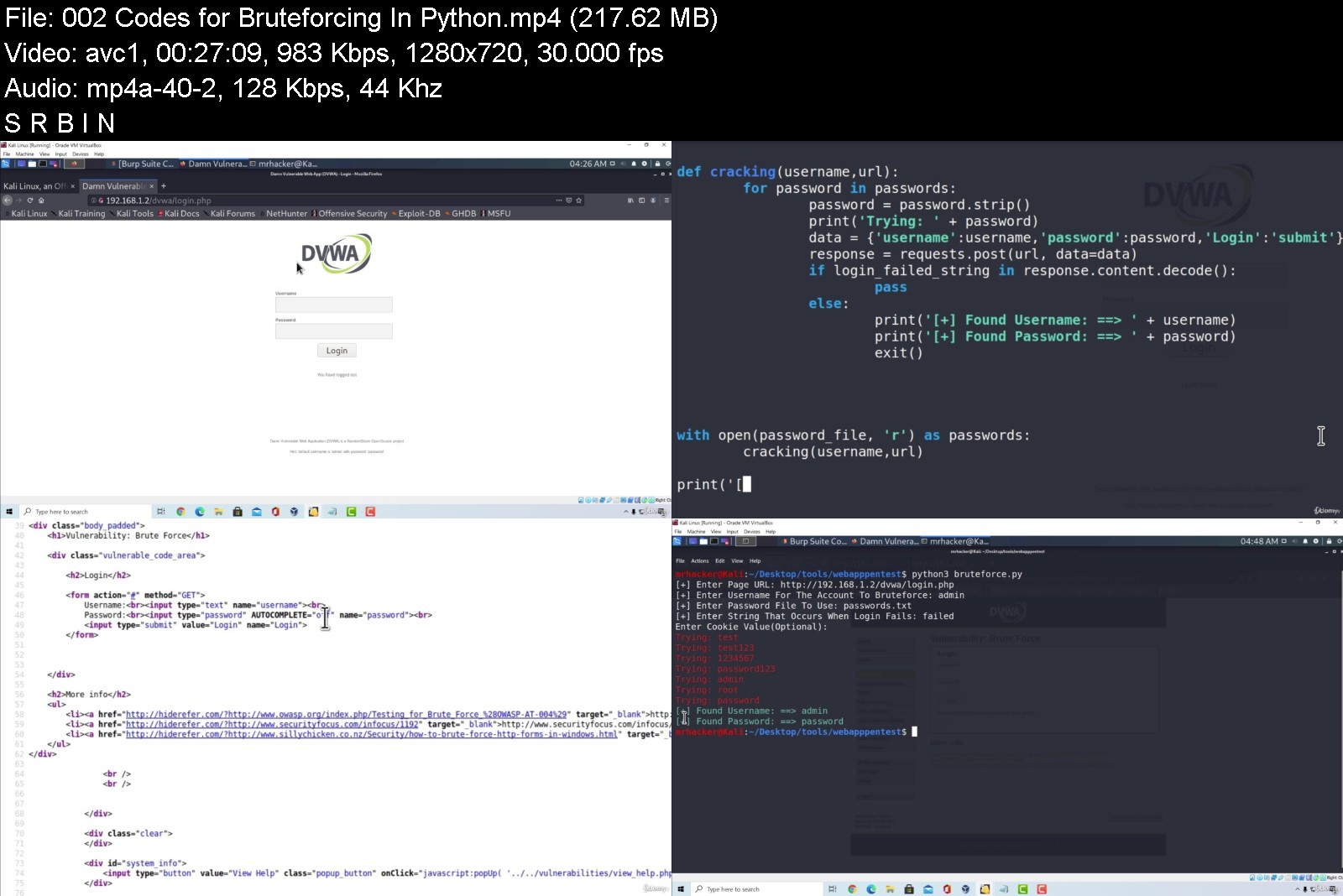
Ethical Hacking
Requirements
You should have a basic knowledge of Internet and its adverse effects.
A computer to install the add-ons, software and to use for setting up your virtual OSINT investigations Lab.
Description
The Internet is a vital tool for investigation, with individuals now sharing more information on themselves than ever. Through the effective use of web browsers, search engines and social media you can find a plethora of information on an individual, this is referred to as Open-Source Intelligence. This course will provide you with a comprehensive understanding of Open-Source Intelligence (OSINT) and has been expertly crafted to cover all of the core basics that you will need to know so that you can conduct your own OSINT investigations.
This course is suitable for anyone in either the public or private sectors, particularly those within law enforcement, corporate security, investigations, journalism and human resources, who are all heavily involved in the collection of information for intelligence purposes.
The course has been developed by an expert in internet-based criminal investigation via Open-Source methods, who has successfully utilized OSINT techniques during both Police and Private investigations. The trainer has a law enforcement background and successfully used the skills demonstrated within this course to identify and locate criminal individuals.
Through this course, you'll learn the best way to set up your machine to conduct investigations, as well as the current techniques utilized in the day to day work of an OSINT professional. This course will demonstrate tools currently available to aid OSINT practitioners in their investigations and research into individuals and businesses. The course also covers Open-Source policy, an often-overlooked section within OSINT training. As well as learning the tools and techniques, it's also crucial to know when you can take action and what action is appropriate; graduates of our training will be educated on policy for Open-Source research and investigation, to ensure knowledge of accepted guidance for individuals acting on behalf of law enforcement or a business. You will also learn the best way to navigate social media as an OSINT investigator, utilizing the latest SOCMINT techniques. You will learn how to search Facebook, Twitter, Instagram, TikTok and LinkedIn to best gather information on your targets.
The Internet has now become all-encompassing; it touches the lives of every human being. We cannot undermine the benefits of Internet, however its anonymous nature allows miscreants to indulge in various cybercrimes. This is a brief Course that explains the cyber laws that are in place to keep cybercrimes in check. In addition to cyber laws, it elaborates various IT Security measures that can be used to protect sensitive data against potential cyber threats.
Cyber Laws are the sole savior to combat cyber-crime. It is only through stringent laws that unbreakable security could be provided to the nation's information. The I.T. Act came up as a special act to tackle the problem of Cyber Crime.
Cyber Crime is committed every now and then, but is still hardly reported. The cases of cyber-crime that reaches to the Court of Law are therefore very few. There are practical difficulties in collecting, storing and appreciating Digital Evidence. Thus the Act has miles to go before it can be truly effective.
At the end of this course, you'll be able to conduct your own OSINT investigations and will have a thorough understanding of the tools at your disposal. Whether you're a solo practitioner just starting out, someone just interested in what an OSINT specialist does or can find out about you, or you're a seasoned professional looking for a refresher and an overview of the best systems currently available, this course will suit your needs.
In this Course, I have tried to cover all the current and major topics related to Cyber Laws and IT Security. Anyone using a computer system and Internet to communicate with the world can use this Course to gain knowledge on cyber laws and IT security.
Who this course is for:
Anyone using a computer system and Internet to communicate with the world can use this tutorial to gain knowledge on cyber laws and IT security.
Intelligence professionals (Researchers, Officers and Analysts)
Investigators, Journalists, Recruitment Departments, Fraud Departments
Anyone seeking an insight into how OSINT practitioners operate, to see what information about you may be available.
Anyone who want to learn the core concepts of Ethical Hacking
https://anonymz.com/?https://www.udemy.com/course/information-security-and-cyber-law/
download скачать from RapidGator
https://rapidgator.net/file/c47d6f794bae9ac2e92610c4230d5e92/Open_Source_Intelligence,_Ethical_Hacking_and_Cyber_Law.part1.rar.html https://rapidgator.net/file/03213c4b7f2976d1af54a61750424329/Open_Source_Intelligence,_Ethical_Hacking_and_Cyber_Law.part2.rar.html https://rapidgator.net/file/1a5344f3d5cdccb6b299b3c0b63c0a1d/Open_Source_Intelligence,_Ethical_Hacking_and_Cyber_Law.part3.rar.html
download скачать from Keep2Share
https://k2s.cc/file/5b7824ee93109/Open_Source_Intelligence%2C_Ethical_Hacking_and_Cyber_Law.part1.rar https://k2s.cc/file/fd30fb7732bbd/Open_Source_Intelligence%2C_Ethical_Hacking_and_Cyber_Law.part2.rar https://k2s.cc/file/e398c2aa50f97/Open_Source_Intelligence%2C_Ethical_Hacking_and_Cyber_Law.part3.rar
Отредактировано Srbin (2023-05-10 15:57:46)

